The Invisible Hand’s Deception: Unmasking Layering and Spoofing in Modern Markets
How Deceptive Market Strategies Exploit Weaknesses in Trading Systems and Surveillance Frameworks
This is the start to a series of deep dives into the different methods of market manipulation. There are a lot of them and new ones are being studied each day. shoot a DM or a comment always here for feedback and great ideasIn the fluorescent-lit trading floor of a hedge fund, deep in the heart of Manhattan, Ethan Kane leaned forward in his ergonomic chair. His eyes darted between multiple screens, each displaying cascading streams of market depth. A rising star at his firm, Ethan had cracked the code on a strategy he called “exploring liquidity pockets.” His managers hailed his uncanny ability to move markets and generate returns.
# Pseudocode for Ethan's layering and spoofing algorithm
market_data = get_market_data()
price_levels = calculate_price_levels(market_data, spread=0.01)
# Place fake orders to create artificial demand/supply
for level in price_levels:
place_order(side='buy', price=level, size=100, cancel_after=0.2) # Cancel after 200ms
# Monitor market reaction
while True:
updated_data = get_market_data()
if price_moves_in_favor(updated_data):
execute_real_trade(side='sell', size=100)
cancel_all_orders()
break
# Cancel remaining orders to avoid fills
cancel_all_orders()But Ethan knew the truth. His strategy relied not on skillful analysis or long-term vision but on exploiting the invisible currents of the market through a carefully choreographed act of deception. By layering orders that would never be filled and creating artificial momentum, Ethan manipulated prices to benefit his genuine trades. What seemed like brilliance was, in fact, a house of cards built on market manipulation techniques known as layering and spoofing.
Understanding Layering and Spoofing
At their core, layering and spoofing exploit the structure and psychology of order-driven markets. These tactics involve placing a series of orders designed to mislead other participants about the true supply and demand. While the terms are often used interchangeably, they have distinct characteristics:
Layering: A trader places multiple orders at various price levels on one side of the market—often far from the prevailing bid or ask—to create the illusion of strong demand or supply. These orders are swiftly canceled once they induce other market participants to act, enabling the manipulator to execute trades on the opposite side of the market.
Spoofing: Similar in intent, spoofing typically involves placing large orders on one side of the market with no intention of execution. The sheer size of these orders can influence market sentiment, prompting other traders to adjust their positions. The spoofer cancels the orders as soon as their objective is achieved.
The Mechanics of Deception
Layering and spoofing rely on a deep understanding of market microstructure, including the workings of order books, matching engines, and the behavior of other market participants. Here's how these strategies are executed:
Order Placement:
Manipulators use high-frequency trading (HFT) systems to place a series of fake buy or sell orders at different price levels. These orders are strategically positioned to appear legitimate and create an artificial imbalance in the order book.
Inducing Market Reaction:
The presence of these orders influences the perception of supply and demand. For example, multiple buy orders can give the illusion of increasing demand, prompting other traders to place genuine orders at higher prices.
Exploiting the Movement:
Once the price moves in the desired direction, the manipulator cancels the fake orders and executes real trades on the opposite side of the market. This allows them to buy low and sell high (or vice versa), profiting from the price fluctuation they engineered.
Order Cancellation:
Speed is critical. Advanced algorithms cancel fake orders milliseconds before they are executed, minimizing the risk of unintended fills.
Advanced Techniques and Tools
Modern manipulators use sophisticated tools to enhance the effectiveness of layering and spoofing:
Latency Arbitrage: Exploiting time lags between different trading venues to manipulate prices in one market and profit in another.
Order Book Analysis: Real-time monitoring of the order book to identify vulnerable patterns and adjust manipulative strategies.
Adaptive Algorithms: Programs that dynamically adjust order size, placement, and duration based on real-time market conditions.
Decoy Orders: Placing smaller orders to test market reactions before deploying larger manipulative strategies.
Detection Challenges
Detecting layering and spoofing requires distinguishing between legitimate trading strategies and manipulative behavior. While regulators and exchanges employ sophisticated methods, the effectiveness of these systems varies greatly. A prime example is FINRA’s Consolidated Audit Trail (CAT), a regulatory initiative designed to track all order and trade activity across U.S. equity and options markets. While CAT is a powerful data aggregator, its approach to surveillance often resembles that of a cybersecurity Security Operations Center (SOC).
Much like a SOC, CAT monitors vast quantities of data in real time, flagging anomalies for further review. However, this framework focuses heavily on surface-level pattern recognition and lacks the depth to identify sophisticated manipulators. For example, traders who understand CAT’s parameters can disguise their intent by adjusting order sizes, placements, and timing to appear as legitimate market participants. CAT’s reliance on pre-defined thresholds and heuristic models means it is inherently reactive, identifying known tactics but struggling to adapt to novel strategies.
Moreover, CAT’s centralized structure and emphasis on compliance reporting make it more effective at post-incident analysis than real-time intervention. High-frequency traders and market insiders who know how to exploit gaps in regulatory oversight can evade detection by staying just within the thresholds of suspicious activity. This limits CAT’s utility in preventing market manipulation, as it is better suited to flagging blunt anomalies than detecting the nuanced patterns used by skilled spoofers and layerers.
Regulators and exchanges currently supplement CAT with machine learning algorithms, but even these systems depend on well-defined inputs, making them vulnerable to circumvention by manipulators adept at exploiting edge cases and systemic blind spots.
Pattern Recognition:
Algorithms scan for recurring patterns, such as rapid order cancellations or clusters of orders at distant price levels.
Anomalous Behavior Analysis:
Surveillance systems flag traders whose actions deviate significantly from their historical behavior or industry norms.
Cross-Venue Monitoring:
Manipulators often operate across multiple trading venues. Regulators analyze data from various markets to identify coordinated activity.
A Case Study in Spoofing
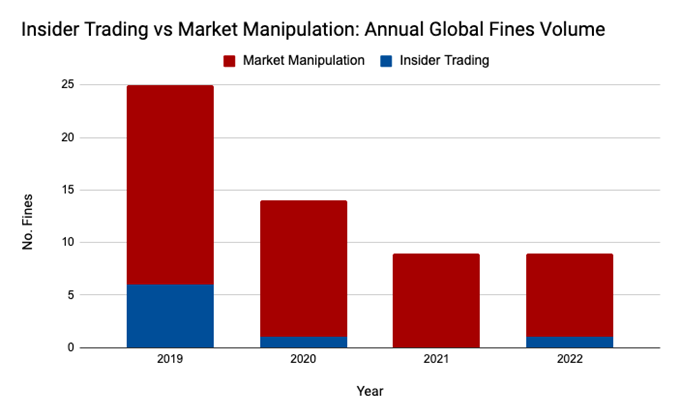
In 2010, the flash crash shook global markets, erasing nearly $1 trillion in equity value within minutes. While multiple factors contributed to the chaos, subsequent investigations revealed the role of spoofing. Navinder Singh Sarao, a British trader, used automated programs to flood the market with spoof orders. His manipulative tactics created artificial liquidity imbalances, driving prices to levels favorable for his trades. Sarao earned millions while destabilizing the broader market, eventually leading to his extradition and conviction.
More recently, in 2020, JPMorgan Chase was fined $920 million for engaging in spoofing practices in precious metals and Treasury markets. The firm’s traders placed large, deceptive orders to manipulate prices, profiting at the expense of other market participants. This high-profile case underscored the ongoing prevalence of such tactics, even among major financial institutions.
The Impact of Layering and Spoofing
The consequences of layering and spoofing extend beyond individual victims. These practices undermine market integrity, erode investor confidence, and distort price discovery. Retail investors, in particular, are vulnerable, as they lack the tools and insights to distinguish genuine market movements from manipulation.
Moreover, the ripple effects can disrupt entire ecosystems. For example, distorted commodity prices can affect producers, consumers, and even national economies. In the case of JPMorgan’s spoofing scandal, the manipulation of Treasury markets had implications for government financing costs and monetary policy.
Lessons from Ethan Kane
Ethan’s meteoric rise came to an abrupt end when his activities triggered an internal compliance review (everyone hates compliance). The algorithms that had once aided his success now turned against him, flagging his behavior as anomalous. Confronted with evidence of his misconduct, Ethan faced not only the loss of his career but also potential legal repercussions.
Ethan’s story serves as a cautionary tale for the financial world. In an era of algorithmic trading and fragmented markets, the line between innovation and manipulation is razor-thin. For traders, firms, and regulators alike, the challenge lies in navigating this complex landscape while upholding the principles of fair and transparent markets.
The Way Forward
As technology continues to transform financial markets, the fight against layering and spoofing will require a multi-faceted approach. Collaboration between regulators, exchanges, and market participants is essential to enhance surveillance capabilities and foster a culture of compliance. Only by addressing these deceptive practices can we ensure the resilience and integrity of global financial systems.
Ethan Kane’s downfall may be an isolated story, but it mirrors broader trends that threaten the foundation of modern markets. The question remains: Will we rise to the challenge, or will the invisible hand of deception continue to guide our markets?